One of the technological solutions that is being used most in the business world is cloud computing. The migration of data and processes to virtual servers has multiple benefits for users, but it also brings with it a major defect: its vulnerability, making it susceptible to security breaches.
Migrating to the cloud offers many advantages, but it also introduces new security challenges. Cloud network security focuses on protecting your networks, applications and data in cloud environments, ensuring that only authorized people have access.
On the Google Cloud page, top cloud computing technology, they explain “Like cloud security, cloud network security refers to the technology, policies, controls and processes that are used. to protect data. The sole objective is to protect cloud networks from unauthorized access, modification, misuse or exposure.”
“Cloud network security is one of the basic layers of cloud security that allows companies to insert security controls, threat prevention and network security to manage the risks of the dissolving network perimeter,” they explain.
Importance of security at the cloud network level
Security when working on any software product is always one of the most important aspects to take into account, especially in technologies that are within a cloud. Cloud networks store and transmit data critical to businesses and users. Guaranteeing the integrity, confidentiality and availability of this data is essential to prevent information leaks and guarantee user privacy.
The cloud allows remote access to resources and services from geographically dispersed locations. This expands the security perimeter and requires strong protection measures to ensure that only authorized people can access resources.
Cloud infrastructures are highly scalable. This means it is critical to control access and connectivity as resources are scaled horizontally or vertically to meet changing demands. Network security must scale similarly.

Within security at the level of cloud networks, regulatory compliance must also be taken into account. Security regulations and standards, such as GDPR, HIPAA, and PCI DSS, impose specific requirements for data protection and network security. Organizations must comply with these regulations, which makes cloud security crucial.
In the cloud, the responsibility for security is shared between the cloud service provider and the customer. The cloud provider takes care of the security of the underlying infrastructure, while the customer is responsible for protecting its applications and data. This requires efficient security management at all levels of the stack.

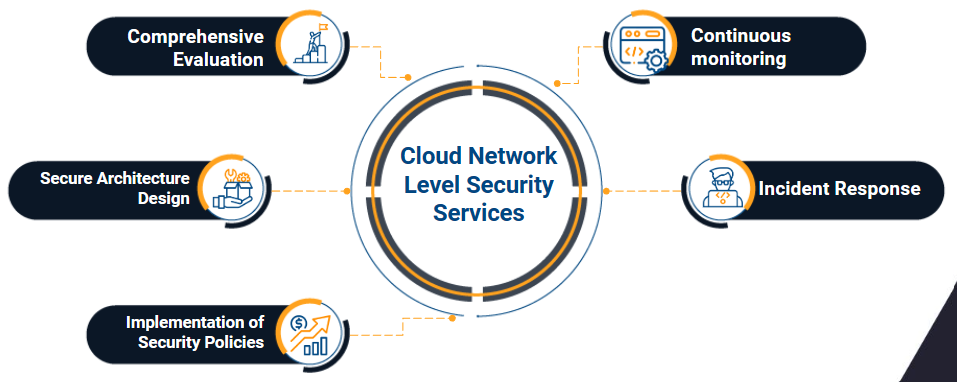
Cloud Network Level Security Services
- Comprehensive Assessment: We begin with a thorough assessment of your cloud infrastructure, identifying vulnerabilities and potential risks.
- Secure Architecture Design: We collaborate with your team to design a secure architecture that meets your business needs and security standards.
- Implementation of Security Policies: We configure security measures, such as firewalls, access controls and intrusion detection, to protect your cloud resources.
- Continuous Monitoring: We maintain constant surveillance of your cloud networks in search of threats in real time, guaranteeing proactive protection.
- Incident Response: We establish incident response plans to address any threat effectively and minimize impact.
Benefits of cloud network security
- Comprehensive Protection: Safeguard your digital assets in the cloud against cyber threats and attacks.
- Regulatory Compliance: Comply with data security and privacy regulations, avoiding legal sanctions and damage to your reputation.
- Continuous Availability: Ensure the continuity of your cloud operations and the accessibility of your services.
- Customer Trust: Demonstrate your commitment to the security of data and services, gaining the trust of your customers.
- Adaptation to Scalability: Cloud network-level security easily adapts to the changing needs of your company as it grows.
Security at the network level in the cloud is essential to protect data, ensure the availability of services and comply with regulations and standards, given the dynamic and constantly evolving environment of cloud computing.
We recommend you on video
