
A software product, anyone worked on, has a weakness that must be attacked from the beginning: its vulnerability to cyber-attacks. Any development team knows this and therefore applies all its knowledge to manage and correct vulnerabilities.
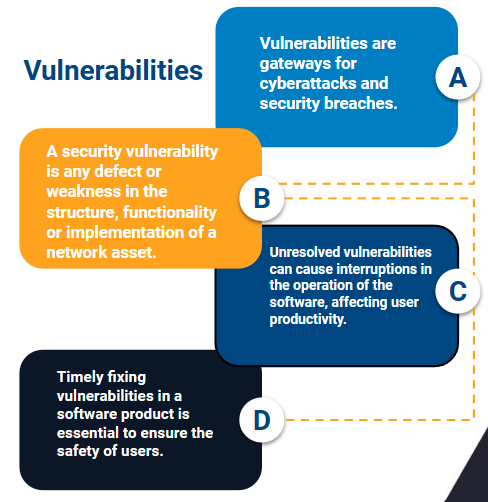
Vulnerabilities are gateways for cyberattacks and security breaches. Effective vulnerability management identifies, prioritizes and fixes these weaknesses before they are exploited by cyber threats, reducing the risk of attacks and the exposure of sensitive data.
What is a security vulnerability?
One of the portals that talks about this topic is IBM. The technology giant explains “A security vulnerability is any defect or weakness in the structure, functionality or implementation of a network or network asset that hackers can exploit to initiate cyberattacks, gain unauthorized access to systems or data, or otherwise harm an organization.”
They also offer some examples of vulnerabilities within a software product: “incorrect firewall configurations that could allow certain types of malware to enter the network, or unpatched bugs in an operating system's remote desktop protocol that could allow hackers will take control of a device.”
Vulnerability Management and Correction Services
At Rootstack we offer several services that help manage the vulnerabilities of a software project, correct them in time and thus avoid a major setback. These are:
- Comprehensive Assessment: We begin with a thorough assessment of your infrastructure, applications and systems in search of known and unknown vulnerabilities.
- Vulnerability Prioritization: We rank vulnerabilities based on severity and risk, allowing you to focus on the most critical ones first.
- Implementation of Patches and Solutions: We correct vulnerabilities effectively, applying patches, updates and customized solutions.
- Monitoring and Verification: We perform continuous monitoring to ensure that vulnerabilities are appropriately addressed and that there are no new weaknesses.
- Training and Awareness: We offer training to your staff so that they understand the importance of safety and contribute to your safety culture.

Benefits of good management and correction of vulnerabilities
- Risk Reduction: Mitigate the risks of cyber attacks by proactively addressing vulnerabilities.
- Data Protection: Safeguard the integrity and confidentiality of your data and the privacy of your clients.
- Regulatory Compliance: Comply with data security and privacy regulations.
- Improved Reputation: Demonstrate your commitment to security, earning the trust of customers and business partners.
- Operational Efficiency: Avoid costly downtime caused by cyber attacks.

Importance of timely correction of vulnerabilities
In addition to the benefits that this service brings to any software project, identifying and correcting any vulnerabilities in time is important since these can be exploited by cybercriminals to access systems, steal data or damage the integrity of the information. Timely remediation of these vulnerabilities protects end users from potential attacks and their consequences.
Remediation of vulnerabilities is usually more economical if done in a timely manner. Leaving them unresolved can increase costs in the long run, as cyber attacks can result in significant financial losses. Also, unresolved vulnerabilities can cause interruptions in the operation of the software, affecting user productivity. Timely correction allows for continued and efficient use of the software.
Software developers and companies have an ethical and professional responsibility to ensure that the products they offer are safe and reliable. Fixing vulnerabilities is a fundamental part of this responsibility.
Timely fixing vulnerabilities in a software product is essential to ensure user security, protect sensitive data, comply with regulations, maintain company reputation, and prevent financial costs and productivity issues.

Dangers to which software is exposed
A software product, whether it is a web application or an e-commerce portal, is exposed to various elements of danger on the Internet, so it must have correct management of its vulnerabilities.
Programming and design errors can lead to vulnerabilities in software that can be exploited by cybercriminals to carry out attacks, such as executing malicious code, infiltrating systems or exfiltrating data. Malicious programs, such as viruses, worms, Trojan horses, and ransomware, can infect software and damage or steal data, as well as disrupt its normal operation.
It is important to note that cybersecurity is a constantly evolving field, and the dangers that software faces change over time. Therefore, it is essential to keep software up to date, follow good secure development practices, and have a proactive security approach to mitigate these dangers and protect software against emerging threats.
We recommend you on video

