When developing a web portal or other software product to which several individuals will have access, care must be taken to preserve the data and all the information it includes, which is why identity and access management is critical.
"Identity and access management, or IAM, is the security discipline that makes it possible for the right entities (people or things) to use the right resources (applications or data) when they need them, without interference, using the devices they want to use." This is what IBM says about the identity and access management process as a whole.
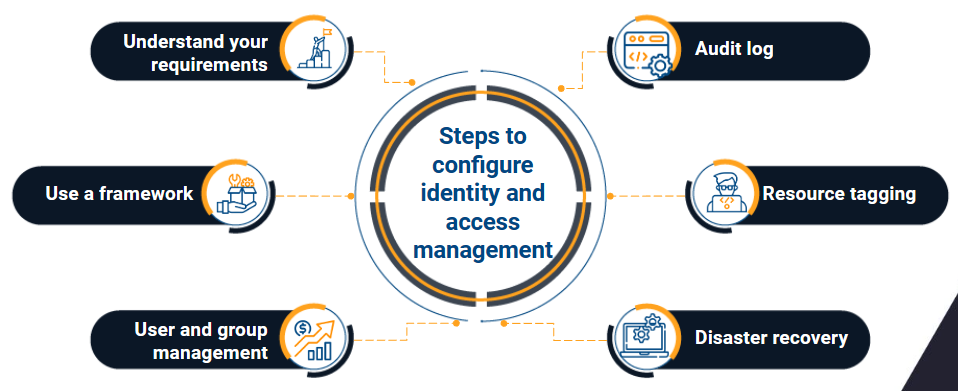
The steps to configure identity and access management
Identity and access management (IAM) is an important part of maintaining the security of your organization's resources and data. IAM allows you to regulate who has access to what information and what actions they can take. Here are some general steps and suggestions for configuring IAM:
Recognize your requirements
Before you start establishing IAM, you should be aware of your organization's access and security needs. Determine which resources require protection, who should have access, and the level of access required.
Make use of a framework
Many cloud providers provide IAM frameworks as well as best practices. Familiarize yourself with the documentation provided by your cloud provider, such as AWS IAM, Google Cloud IAM, or Azure IAM.
PoLP (Principle of Least Privilege)
Use the least privilege principle. This entails giving users and services the bare minimum of access required to do their tasks. Avoid policies that are unduly permissive.
Management of users and groups
Create users and groups in a rational manner and allocate permissions to groups rather than individuals. This increases the scalability of management.
MFA stands for multi-factor authentication
MFA should be required for all users, especially privileged accounts. This gives an extra layer of protection.
Audit trail
Enable comprehensive logging for all IAM actions. This will aid in the monitoring and investigation of security incidents.
Policies should be reviewed and revised on a regular basis
IAM policies should develop in response to your organization's needs. Review and adjust policies on a regular basis to ensure they meet your current needs.

Use roles to provide services
When possible, use IAM roles instead of long-term access keys for services and apps. This decreases the possibility of hidden disclosure.
Resource categorization
Consider using resource tags to organize and control resource access. This is especially helpful in larger settings.
Policy enforcement should be automated
To enforce IAM policies, use automation technologies. This can help to assure compliance while also reducing human error.
Permissions for testing
Before implementing modifications or granting permissions, make sure things perform as intended in a secure environment.

Recovery after a disaster
Prepare disaster recovery scenarios that include IAM setups. Make sure you have backup access options in place in case of IAM difficulties.
Training and documentation
Document your IAM policies and train your team members on best practices in IAM. Maintaining safety requires a well-informed staff.
Maintain your knowledge
Keep up with the latest IAM features and vulnerabilities, as well as security best practices. Security is a field that is always changing.
Tools provided by third parties
Third-party IAM management applications can provide additional functionality and ease of use.
Regulations and Compliance
Ensure that your IAM configurations adhere to industry rules as well as any special requirements that your organization may have.
Keep in mind that IAM is an ongoing process. Monitor, update, and change your setups on a regular basis to suit emerging threats and changing business demands. Security should be prioritized, and IAM is an important component of a robust security posture.
We recommend you on video