The growing adoption of remote work has transformed workplace dynamics, allowing for unprecedented flexibility but also posing significant challenges in terms of cybersecurity. In this context, companies that use IT staff augmentation teams to cover their technological needs must prioritize robust cybersecurity strategies.
Below, we'll explain how organizations can strengthen their defenses in the remote work environment by collaborating with external IT teams.
How to reinforce cybersecurity at work with an IT staff augmentation team
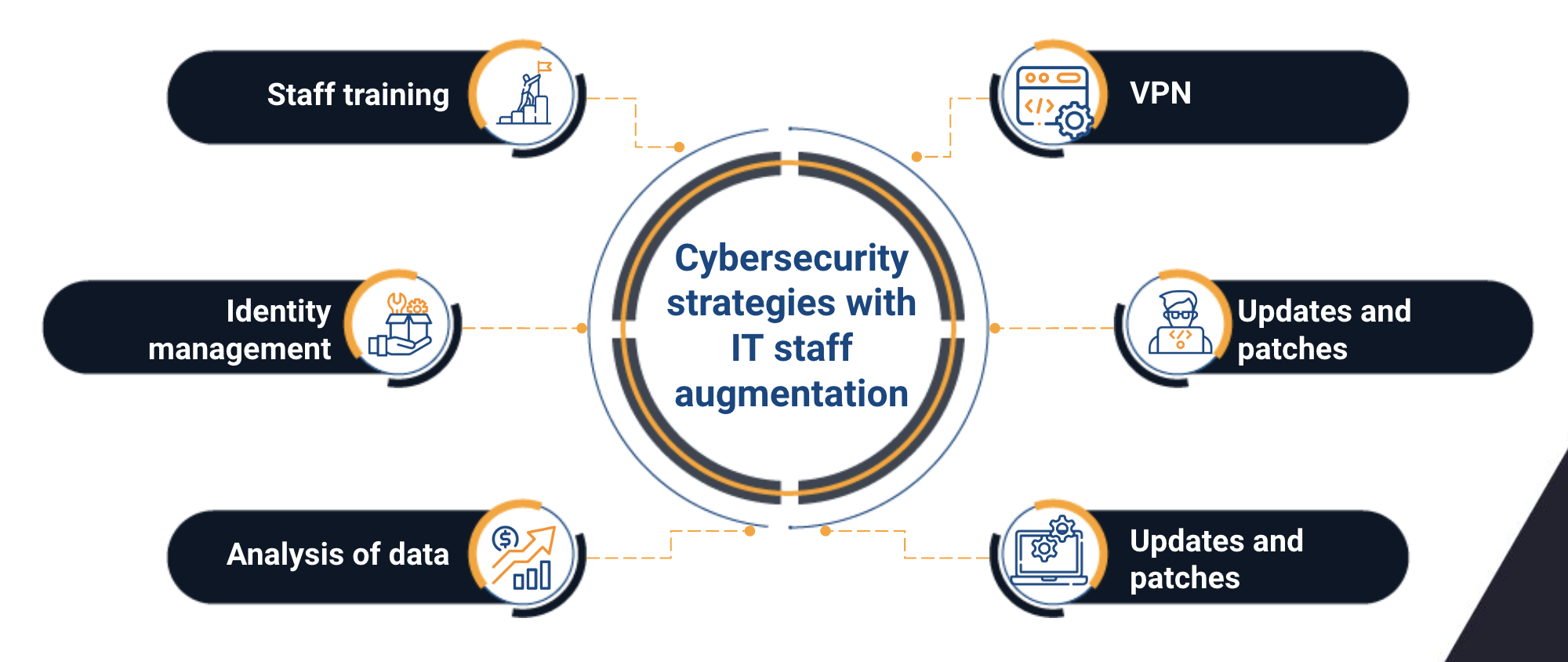
1. Awareness and training of staff:
The weakest link in any cybersecurity strategy is the human factor. Regular training and awareness on cybersecurity practices is crucial. This includes educating remote staff, both internal and external, about common threats, the importance of strong passwords, phishing detection, and protecting sensitive data.
2. Secure Access and Identity Management:
Secure access to systems and data is essential. Implementing two-factor authentication (2FA) and identity management practices helps ensure that only authorized people have access to sensitive information. IT staff augmentation teams must integrate seamlessly into these security protocols, ensuring controlled and audited access.
3. Use of Virtual Private Networks (VPN):
VPNs are a fundamental tool to guarantee the security of communication between remote computers and the company's servers. They ensure that transmitted data is encrypted and protected against possible threats. Collaborating with an IT staff augmentation team requires establishing clear policies on VPN use to ensure a secure connection at all times.

4. Software Updates and Patches:
Keeping all systems, applications and software up to date is an essential preventive measure. Security breaches often occur due to lack of updates. Both internal and external teams must follow a strict protocol to apply security patches and timely updates.
5. Continuous Monitoring and Data Analysis:
Implementing continuous monitoring and data analysis solutions can identify unusual patterns or suspicious activities. This is crucial to detect potential threats in real time. Collaboration with an IT staff augmentation team must include the integration of these solutions into the existing technological infrastructure.
6. Data Backup and Recovery:
Cyber threats, such as ransomware, can compromise data integrity. Establishing regular backup policies and a disaster recovery plan is essential. Ensuring that the IT staff augmentation team is aware of and actively participates in the implementation and testing of these plans ensures an effective response to any incident.
7. Evaluation and Compliance with Regulations:
It is essential to regularly evaluate cybersecurity policies to ensure they comply with relevant industry regulations and standards. This is especially important in regulated sectors such as healthcare or finance. An IT staff augmentation team must operate in compliance with these regulations to ensure security and legality.
8. Transparent Collaboration:
Open and transparent communication between the internal team and the IT staff augmentation team is essential. This includes immediate notification of any security incidents and collaboration in problem resolution. A collaborative approach strengthens cyber defenses and fosters a culture of security throughout the organization.
In the remote work environment, cybersecurity becomes a fundamental pillar for the sustainable success of any organization. Collaborating with IT staff augmentation teams not only expands technological capabilities, but also presents specific challenges that must be addressed with solid strategies.
By implementing proactive measures, raising awareness, and ensuring transparent collaboration, businesses can strengthen their cyber defenses and take full advantage of the potential of a remote IT team. Ultimately, security and performance go hand in hand in today's digital landscape, and adopting effective cybersecurity strategies is essential to ensure long-term success.
Do you need an IT staff augmentation team for your next project? At Rootstack, we have +12 years of experience supporting companies in their digital transformation. Contact us!