
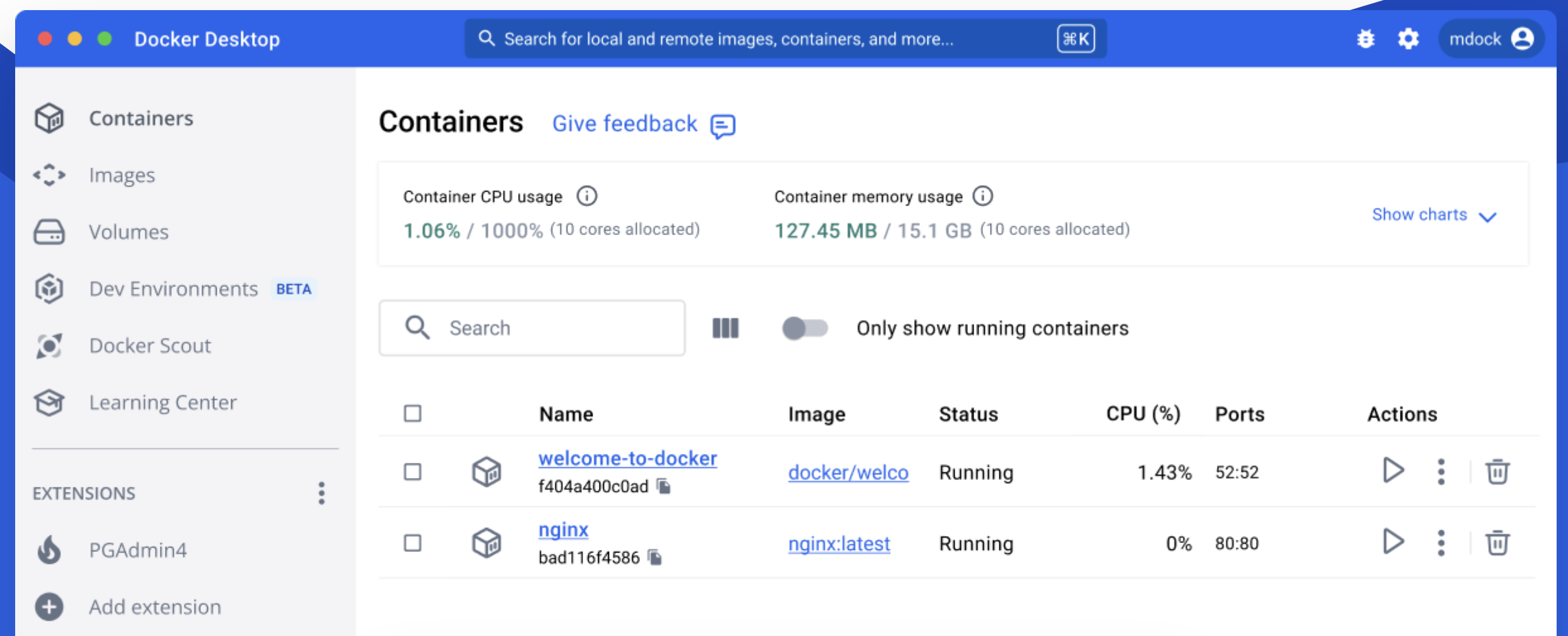
Containers have revolutionized the way businesses develop and deploy applications. However, container security remains a critical concern for business leaders, as any vulnerability can translate into serious threats to the organization.
“Globally, 41 percent of respondents reported a concern about container security in relation to the lack of compliance certifications for containers and privacy breaches”, they noted in a Statista report.
In this article, we will discuss what containers are, why it is crucial to protect them, and best practices to ensure their security in 2024.

What are containers?
Containers are a technology that allows applications to run consistently across different environments, such as development, testing, and production environments. Unlike virtual machines, containers are lightweight and share the host operating system core, making them more resource-efficient.
Tools such as Docker and Kubernetes have popularized the use of containers, allowing companies to scale and streamline software development.
For managers and business leaders, understanding how containers work is key, as their adoption can offer competitive advantages in terms of development speed, efficiency, and flexibility.
Importance of Container Security
The popularity of containers has not gone unnoticed by cybercriminals. Containers, being interconnected and operating in dynamic environments, present additional attack surfaces that can be exploited.
If proper security measures are not in place, companies can face data leaks, application integrity compromises, and potential regulatory compliance violations.
CEOs and business leaders should consider container security not just as a technical responsibility, but as an integral component of the company's security strategy. A successful attack could impact reputation, customer trust, and financial results.
Best practices for container security in 2024
1. Use secure and verified container images
The first step towards container security is to ensure that the images used are trustworthy. Container images can be downloaded from public repositories, but not all have been audited for security. Using official or verified images, preferably those with digital signatures, minimizes the risk of introducing vulnerabilities.
It is vital that IT managers and business leaders implement strict policies on the provenance of images and consider automated scanning tools that detect potential risks.
2. Maintaining a continuous update cycle
A key practice for securing containers is maintaining a consistent update cycle. As new vulnerabilities are discovered, it is crucial that container images and runtimes are regularly updated to mitigate security risks.
IT teams should be on the lookout for security alerts and proactively update underlying software and container images.
Leaders and managers should ensure their teams have automated update processes in place, such as integrating CI/CD tools that validate and update containers quickly.

3. Applying the principle of least privilege
Container security is strengthened by applying the principle of least privilege. This means that each container should only have access to the resources it needs to function, and nothing more. By restricting privileges, the attack surface is reduced, making it difficult for an attacker to expand their control if they compromise a container.
For business leaders, this strategy is essential to ensure that risks are limited and that security policies are enforced across the organization.
4. Continuous monitoring and logging of containers
Constant monitoring of container activity is a critical practice to detect anomalies or intrusion attempts in real time. Monitoring solutions such as Prometheus and Grafana, combined with logging tools such as Fluentd, allow companies to have complete visibility into the behavior of their containers and alert security teams to any suspicious activity.
Incorporating these systems into business processes not only protects data and systems, but also demonstrates the company's commitment to security.
5. Use container-specific security tools
In 2024, the market offers a wide range of tools specialized in container security, such as Aqua Security, Twistlock, and Sysdig. These tools are designed to integrate security directly into the container lifecycle, offering vulnerability scanning, behavioral analysis, and security policy enforcement capabilities.
Business leaders should ensure their teams use these solutions and conduct regular audits to ensure their containers are protected against emerging threats.
Managing Security in Kubernetes
Kubernetes, as a container orchestration platform, introduces an additional layer of complexity to security. As more organizations adopt Kubernetes, it is essential to understand the associated risks and how to mitigate them. Some best practices include:
- Configuring appropriate roles and permissions using RBAC (Role-Based Access Control).
- Segmenting the container network to minimize the impact of potential breaches.
- Enforcing network policies that control traffic between pods.
Business leaders deploying Kubernetes must prioritize security from the start as this platform becomes the core of their technology operations.

Automating Security in the Development Lifecycle
One of the great advantages of containers is their integration with DevOps methodologies. In 2024, security must be an integral part of the development cycle through automation. The DevSecOps approach allows security testing to be performed continuously throughout development, reducing the risk of vulnerabilities.
CEOs and managers should encourage the adoption of these practices in their development teams to ensure that products are not only delivered quickly, but also securely.
Preparing for the Future of Container Security
Container security is a critical aspect for companies looking to take full advantage of this technology. By implementing these best practices, business leaders can ensure that their container environments are resilient against emerging threats and continue to support growth and innovation. Security should be seen not as a barrier, but as an enabler of trust and success in today's digital world.

